Learn what happens behind the scenes when you enter a URL in 2025—DNS, HTTP, IP, and how websites load in seconds. Simple and beginner-friendly!
Introduction
Have you ever wondered what actually happens when you type a web address into your browser and hit Enter? The internet seems like magic—yet it runs on precise, logical steps. If you’re starting your journey into cybersecurity, understanding how the internet works is non-negotiable.
In this guide, we’ll break down the foundational internet concepts every aspiring cybersecurity professional must understand—no tech jargon overload, just clarity.
1. The Big Picture: How the Internet Works
At its core, the internet is a global network of connected computers. Each device is assigned an IP address and communicates using standard rules called protocols.
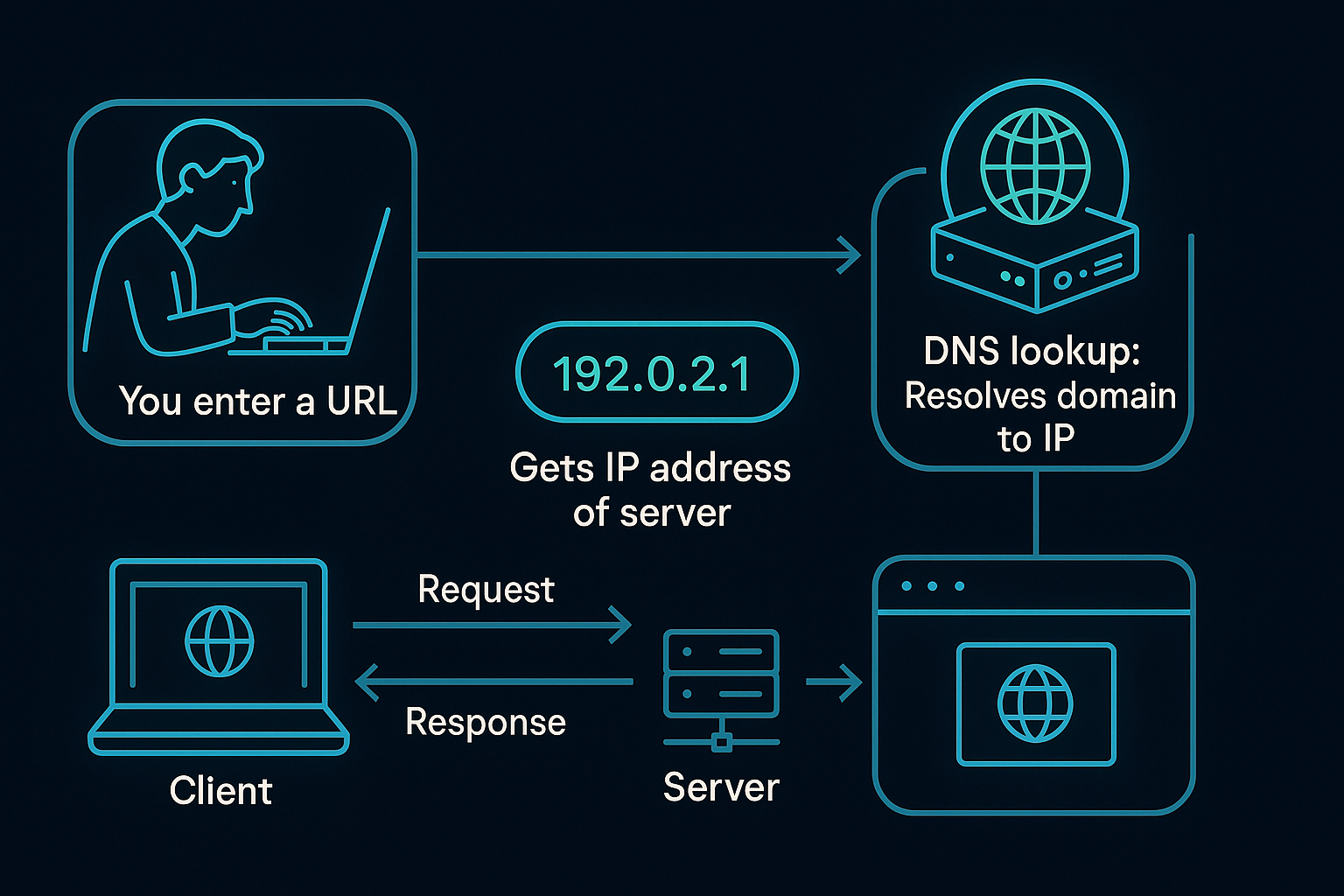
When you type a URL like www.cyberhackacademy.com, a series of invisible steps happen:
- Your browser checks if it has the address saved in cache.
- If not, it asks a DNS server to find the IP address for that domain.
- Once it has the IP, it sends a request over the internet.
- The server hosting that website receives the request and responds.
- The data (the website) travels back and loads in your browser.
Let’s unpack each part.
2. What Is a URL and Why Is It Important?
A URL (Uniform Resource Locator) is the web address you type. For example:
https://www.cyberhackacademy.com/blog
It breaks down like this:
https://– Protocol (explained below)www.cyberhackacademy.com– Domain name/blog– Specific path or page
Think of a URL as the full address to a house, telling your browser exactly where to go and what to fetch.
3. What Is DNS? The Internet’s Phonebook
DNS stands for Domain Name System. It’s like the phonebook of the internet.
We humans remember names like google.com, but computers talk using IP addresses like 142.250.190.78.
So when you type a domain, your device asks a DNS server:
“Hey, what’s the IP address of
www.cyberhackacademy.com?”
The DNS server responds with the IP, and now your browser knows where to send the request.
4. IP Addresses and Ports: The Internet’s Addressing System
✅ What Is an IP Address?
An IP (Internet Protocol) address is a unique identifier for every device on a network.
- IPv4 looks like this:
192.168.1.1 - IPv6 (newer and longer):
2001:0db8:85a3:0000:0000:8a2e:0370:7334
It’s like your home address—but for your device.
✅ What Is a Port?
If the IP address is the house, ports are like apartment numbers.
Each service (like web, email, FTP) runs on a different port. For example:
- Port 80 – HTTP (regular websites)
- Port 443 – HTTPS (secure websites)
- Port 25 – Email (SMTP)
So when your browser contacts an IP, it also targets a specific port to reach the correct service.
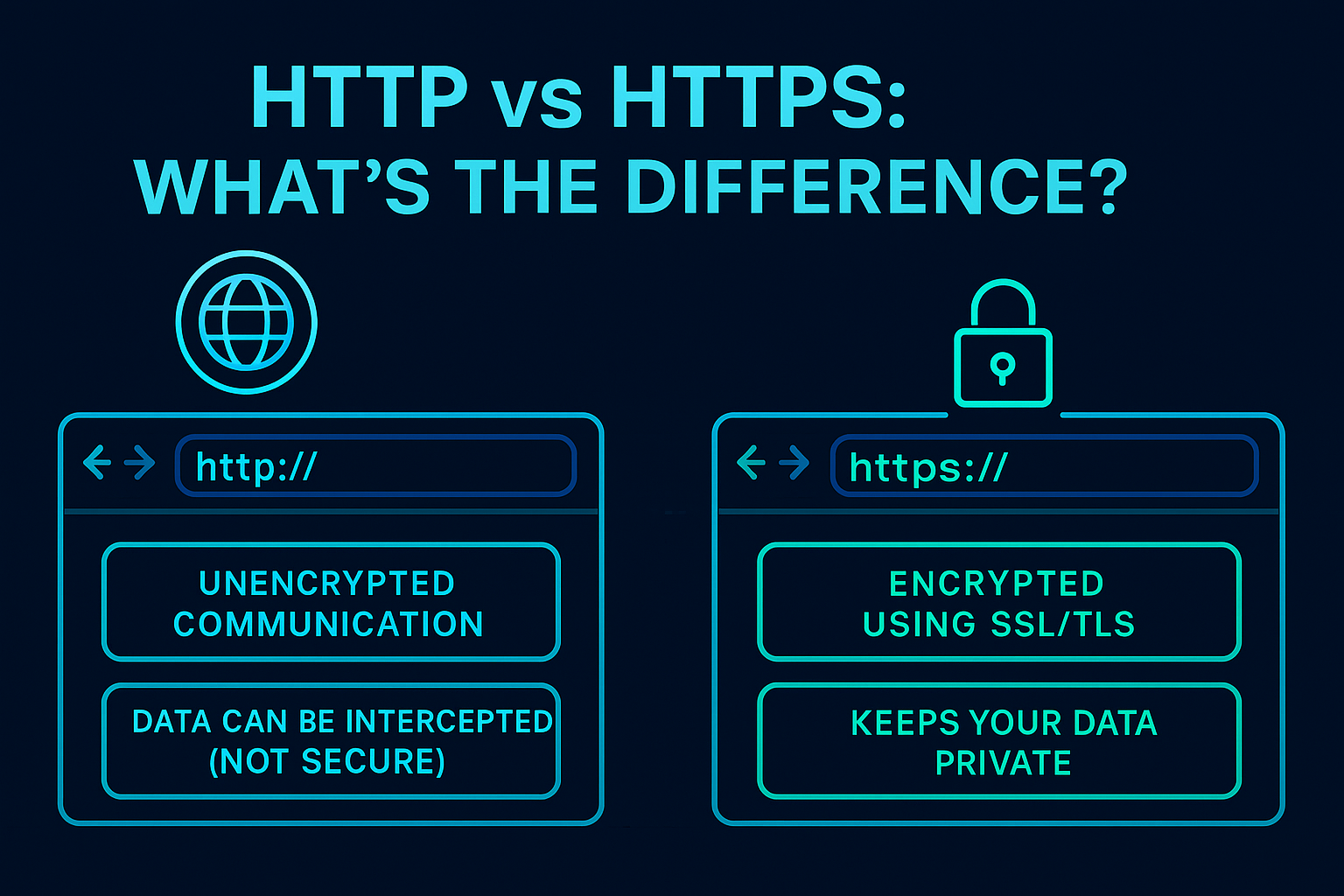
5. HTTP vs HTTPS: What’s the Difference?
✅ HTTP (HyperText Transfer Protocol)
- Unencrypted communication
- Data can be intercepted (not secure)
✅ HTTPS (HTTP Secure)
- Encrypted using SSL/TLS
- Keeps your data private
- Essential for login forms, online shopping, etc.
Always look for HTTPS when browsing—especially on sensitive websites.
6. The Client-Server Model: How Devices Communicate
Every time you access a website, your device (the client) sends a request to a server.
- The client = your browser/device
- The server = computer hosting the website
Steps in the process:
- Your browser (client) sends a request to the server via IP/port.
- The server processes the request.
- It sends back a response (HTML, images, etc.).
- Your browser renders the content.
This is known as the client-server model—a foundational concept in cybersecurity and networking.
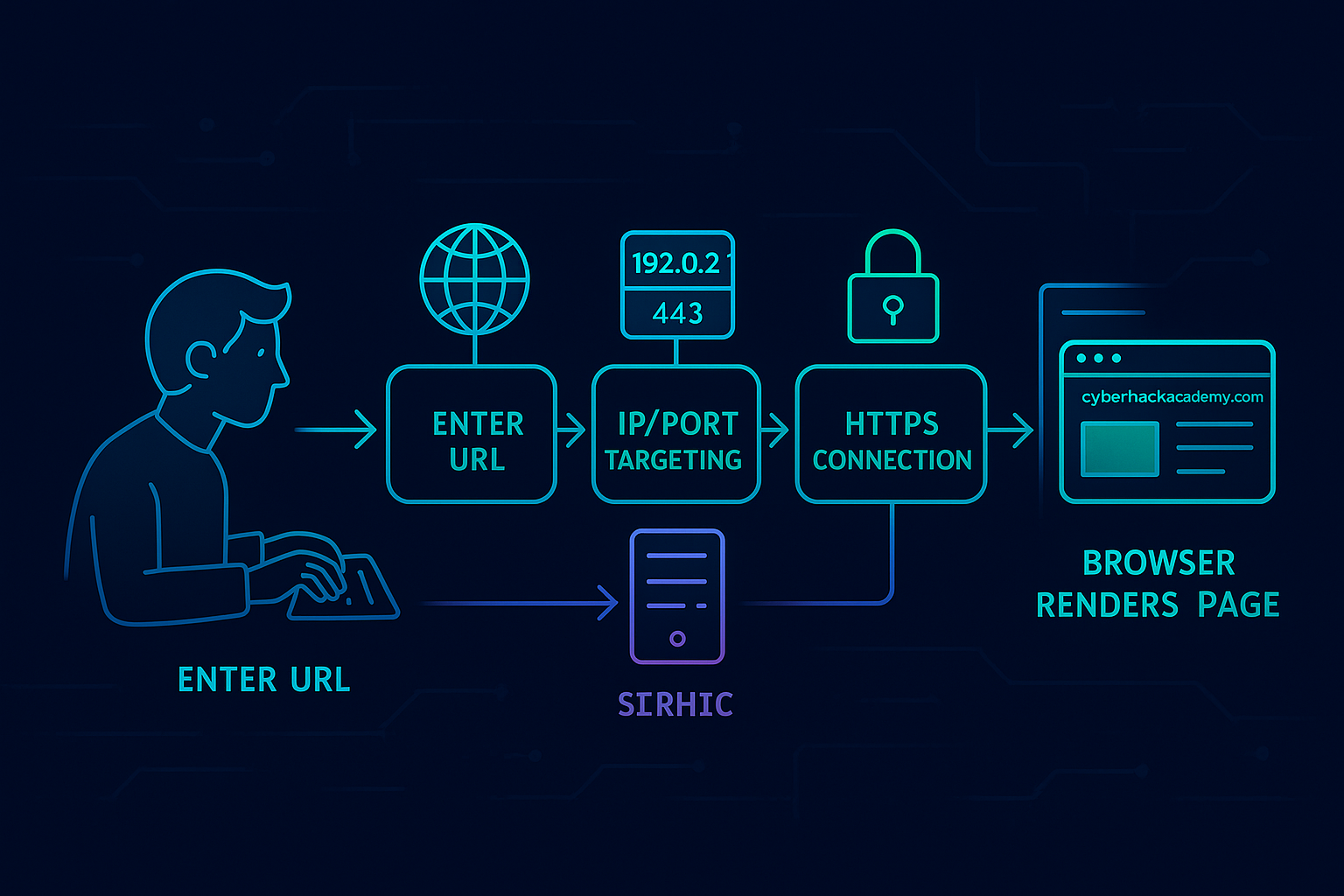
7. Real-World Example: Loading CyberHackAcademy.com
Let’s connect all the dots with a real-world example:
- You type
www.cyberhackacademy.com. - Browser checks DNS to get the IP address.
- It sends a request to that IP using port 443 (HTTPS).
- The server receives the request and sends back the homepage.
- Your browser displays the site—and you start learning cybersecurity!
🔧 Try It Yourself: Practical Tools to Understand How the Internet Works
Reading is good, but doing is better. Here are some free tools you can use to see what really happens when you enter a URL in your browser—step by step.
🧭 1. DNS Lookup Tools (See How Domain Names Turn Into IPs)
- 🌐 DNS Checker – Check DNS records from multiple global locations
- 🌐 NSLookup.io – Get detailed DNS results (A, MX, CNAME, etc.)
- 🌐 Google DIG Tool – DNS troubleshooting by Google
🌐 2. Find Your IP & DNS Info
- 🌐 WhatIsMyIP.com – See your public IP, ISP, and location
- 🌐 IPInfo.io – Learn more about your own IP and hostname
- 🌐 DomainTools WHOIS – Look up domain ownership and info
🔍 3. Simulate Real Web Requests
- 🌐 Geekflare HTTP Header Tool – View full request/response headers
- 🌐 Request Inspector – Inspect how data is sent and received
- 🌐 ReqBin – Test HTTP methods like GET, POST, PUT, DELETE
🖥️ 4. Visualize How the Internet Works
- 🌐 How DNS Works (Comic) – A fun, illustrated journey through the DNS
- 🌐 Kaspersky CyberMap – Watch global internet traffic and attacks in real time
🖥️ 5. Try It Locally on Your Terminal or Command Line
Want to simulate what your browser does behind the scenes? Run these commands on your computer:
On Windows:
nslookup cyberhackacademy.com
ping cyberhackacademy.com
tracert cyberhackacademy.com
On Linux/macOS:
nslookup cyberhackacademy.com
ping cyberhackacademy.com
traceroute cyberhackacademy.com
💡 Tip:
Use these tools often. The more you see, the better you’ll understand—which is essential for any future cybersecurity expert.
🧠 Conclusion
Understanding what happens when you enter a URL is your first real step into the world of how the internet actually works. Behind every website you visit is a chain of systems—DNS, IP addresses, ports, protocols, and servers—all working in perfect sync to deliver data.
Now that you’ve got the theory down, you don’t have to stop here. Scroll back to the “Try It Yourself” section and use those tools to see the internet in action. Practice makes knowledge stick—and in cybersecurity, hands-on experience is everything.
So next time you hit Enter on a web address, you won’t just see a website—you’ll see a digital handshake, a journey across servers, and a system of protocols you now understand.
You’ve just unlocked the first building block in your cybersecurity journey. Let’s keep going.
✅ Key Terms Recap
- URL – A web address
- DNS – Translates domain names to IP addresses
- IP Address – Unique identifier for devices
- Port – Identifies specific services on a device
- HTTP/HTTPS – Protocols for web communication
- Client-Server Model – How devices request and respond
