Learn how cyberattacks unfold through the 7 stages of the cyberattack lifecycle and discover how security teams can disrupt attackers at each step.
Introduction: Understanding the Cyberattack Lifecycle
In the world of cybersecurity, understanding how hackers operate isn’t just useful—it’s essential. Most cyberattacks don’t happen randomly; they follow a structured plan called the Cyberattack Lifecycle, also known as the Cyber Kill Chain. Originally developed by Lockheed Martin, this model outlines each stage an attacker goes through, from planning to execution.
Whether you’re a student, a cybersecurity enthusiast, or a professional, this guide will help you understand how attacks happen and how defenders can intercept them at every stage.
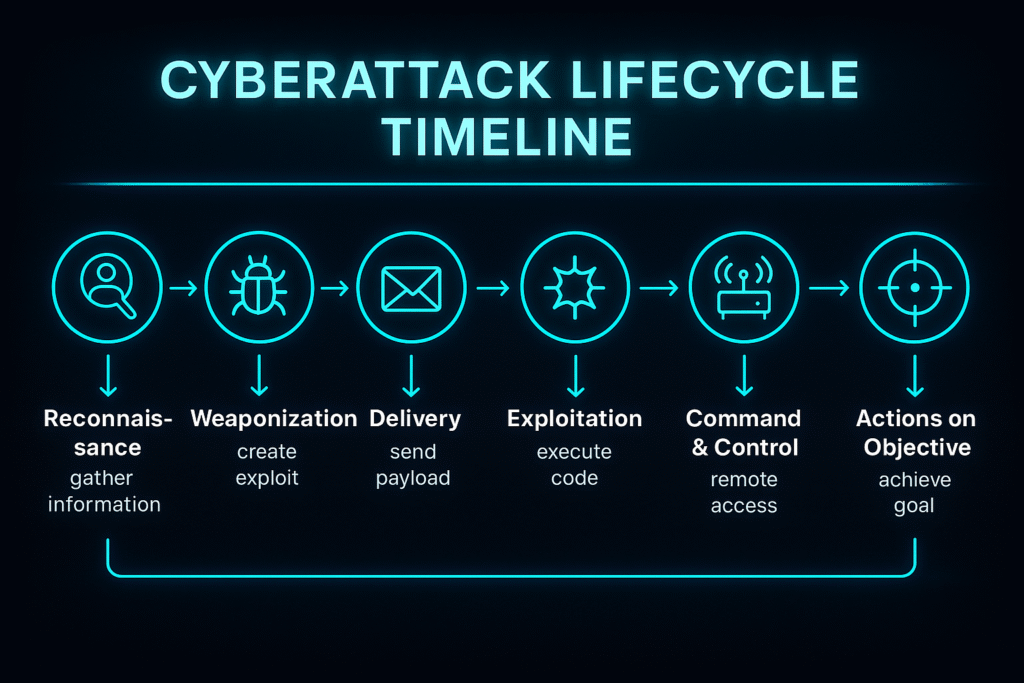
Stage 1: Reconnaissance
Goal: Gather as much information as possible about the target.
This is the planning phase. Hackers use tools and techniques to gather data such as employee names, email formats, exposed servers, and software vulnerabilities.
Tools & Techniques:
- Google Dorking
- WHOIS lookups
- Shodan
- Social media profiling
- Nmap scans (Nmap.org)
Defensive Measures:
- Limit public exposure of sensitive data
- Use honeypots to mislead attackers
- Monitor for excessive scanning activity
Stage 2: Weaponization
Goal: Build the malware or exploit to use against the target.
Once information is collected, attackers create payloads such as trojans, ransomware, or backdoors. These are usually customized for the specific target.
Example Payloads:
- Remote Access Trojans (RATs)
- Exploit Kits (e.g., Metasploit)
- Malicious Office documents
Defensive Measures:
- Keep software up to date
- Use sandboxing and malware analysis tools
- Subscribe to threat intelligence feeds
Stage 3: Delivery
Goal: Deliver the malware to the victim.
The attacker now sends the payload to the target. Common delivery channels include:
Methods:
- Phishing emails
- Infected websites (drive-by downloads)
- Malicious USBs
Defensive Measures:
- Email filters and spam detection
- DNS filtering and firewalls
- Security awareness training for employees
Stage 4: Exploitation
Goal: Execute the malware or exploit a system vulnerability.
Once delivered, the malware exploits a flaw in the system or tricks the user into running it.
Exploitation Tactics:
- Exploiting unpatched software
- Tricking users into enabling macros
- Zero-day vulnerabilities
Defensive Measures:
- Patch management
- Endpoint Protection Platforms (EPP)
- Disable unnecessary features (e.g., macros)
Stage 5: Installation
Goal: Establish persistence within the system.
The malware is now installed, allowing the attacker to maintain access even after reboots.
Persistence Techniques:
- Registry changes
- Scheduled tasks
- DLL injections
Defensive Measures:
- Use Endpoint Detection & Response (EDR) tools
- Monitor system changes
- Employ least privilege principles
Stage 6: Command and Control (C2)
Goal: Establish a remote connection to control the infected system.
The malware communicates with a Command and Control server, allowing the attacker to send commands or download more malicious tools.
Indicators of C2:
- Strange outbound traffic
- Communication with known malicious IPs
- Use of unusual ports
Defensive Measures:
- Network segmentation
- Intrusion Detection Systems (IDS)
- Monitor outbound traffic
Stage 7: Actions on Objectives
Goal: Achieve the final goal—data theft, system takeover, or sabotage.
This is the endgame. The attacker now takes action based on their motive.
Common Objectives:
- Exfiltrating sensitive data
- Encrypting files for ransom
- Deleting critical infrastructure
Defensive Measures:
- Data Loss Prevention (DLP)
- Regular backups
- Incident Response (IR) planning
🔎 Real-World Example: Phishing to Ransomware
Imagine an attacker targeting a healthcare provider:
- Reconnaissance: Research staff on LinkedIn.
- Weaponization: Craft a ransomware-loaded Excel file.
- Delivery: Email it as a fake billing invoice.
- Exploitation: User enables macros and triggers the payload.
- Installation: Ransomware encrypts files.
- C2: Malware communicates with attacker.
- Objective: Victim receives a ransom demand.
This example shows how each stage flows into the next.
🏛️ Timeline Infographic
🔗 Read More:-
- Cybersecurity Fundamentals: What Are Threats, Vulnerabilities & Attacks? (2025)
- What is the CIA Triad? Everything you need to know! Cybersecurity Basics (2025 Edition)
🌐 External Links
📚 Conclusion: Think Like a Hacker, Defend Like a Pro
The Cyberattack Lifecycle helps us break down the complexity of modern hacking into manageable, understandable stages. For students, professionals, and cybersecurity teams, knowing this lifecycle is key to building effective defenses.
Want to stay ahead of hackers? Subscribe to CyberHack Academy for daily tutorials, threat analysis, and more beginner-to-pro content.
